Introduction
Welcome to the application security course.
Principle
The course is in a self-learning format, where all the required material is written in the website.
Small exercices with increasing difficulty will be provided. These exercices will be automatically corrected by the Moulinette, and are mandatory.
I will be available to guide (not give the whole valid answer) students if they are blocked. The goal obviously is to teach students to work by themselves, read documentation, and think by themselves.
All technical terms will be explained with sufficient depth to progress and validate all exercices. If explanations are not detailed enough, or for the more curious students, I invite you to find more resources on the Internet.
Requirements
- Basic knowledge in C programming language
- Basic knowledge in Python programming language
Disclaimer
⚖ Ethics, Laws
Techniques learned in this course will give students the ability to attack applications and systems. The course is provided for educational purpose only. Students must not attack applications outside of this course. Always abide by the law, and ask for authorization before assessing an application / system.
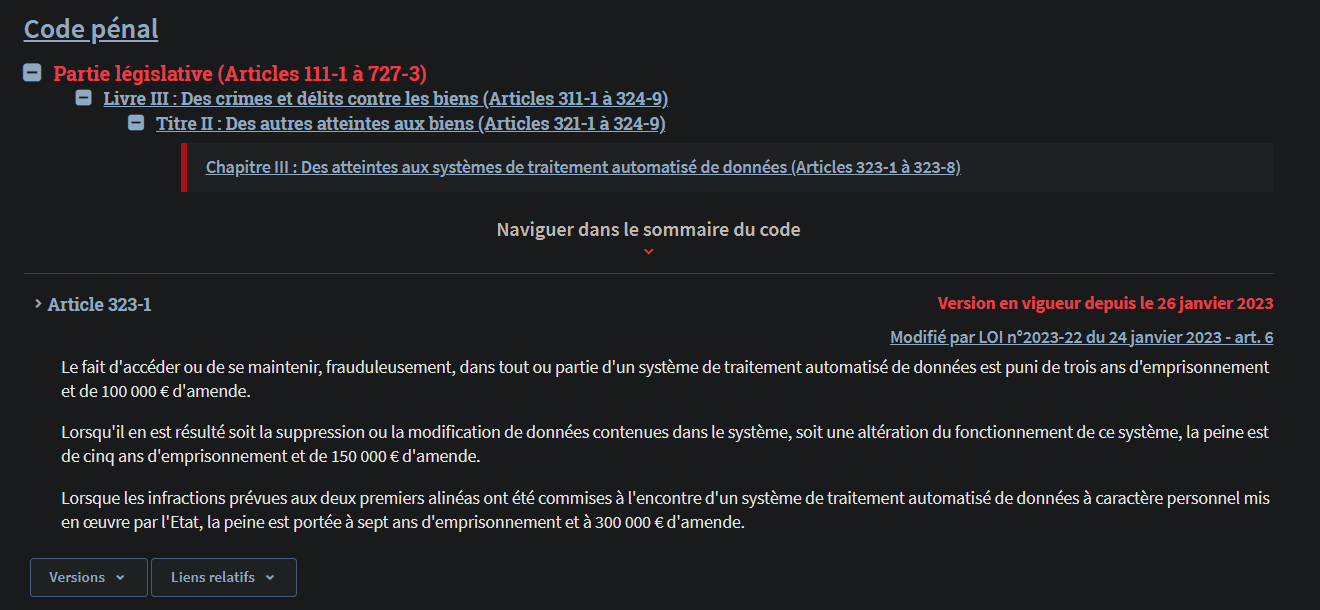
In France, unlawfully getting access inside an online system can be punished, with jail time up to 5 years and a 100 000 euros fine.
💼 Course material
This course belongs exclusively to Michel SAN, and cannot be shared without authorization.
Any material presented in this website was made by Michel SAN, and is not linked in any way to any of his employers, current or future.
Plan
👾 Introduction to binary exploitation
The goal of this chapter is to understand how C manages memory, and how we can exploit its vulnerabilities to take control of the execution flow, and even execute our own code.
The overview will look like this :
- memory management in C (stack)
- strings management in C
- disassembling
- decompiling
- shellcode
- stack-based buffer overflow
- format string vulnerability, with arbitrary read and write
🛡 Secure programming in C
The goal of this chapter is to show different possible mitigations during :
- programming
- compilation
Overview:
- handle user inputs and strings securely in C
- Stack canary
- ASLR
- PIE
- No Execute
Grading
Each chapter will have automatically corrected exercices (by the Moulinette).
They will count for 40% of the final note.
Additionally, an on-premises timed assessment will be made (CTF like) at the end of the course.
Cheating will not be tolerated, it will be severely sanctionned and reported to the administration.
Internet access as well as personal notes will be allowed during the on-premise assessment (just like in real life). But no collaboration during the assessment ! It will be an individual assessment of skills.
Collaboration
Collaboration is allowed during practical sessions. Collaboration is defined as such :
- verbal communication (not too loud please)
- brainstorming
- instant messaging
But do not stupidly copy someone else's exploit.
If a hard exercice is validated from the lab, but not during the assessment, the student will have to explain why. So if you do validate an exercice from the lab, make sure that you have fully understood the exercise.